AirTags: The Strained Privacy
And on the surface the system is designed to protect privacy. But not all that glitters is gold. Let's scratch that surface a bit.
While AirTags are designed to protect the owner, they do not protect against malicious owners. The simplest use case is that I buy an AirTag and drop it in a pocket of a person I want to track. Instantly I have that person pinpointed on a map, in real time. A stalker's dream. Technically if that person happens to have an iPhone, it will eventually start alerting about a "foreign" tracking device she carries, but that is only on an iOS device. Non-iOS users are in the cold.
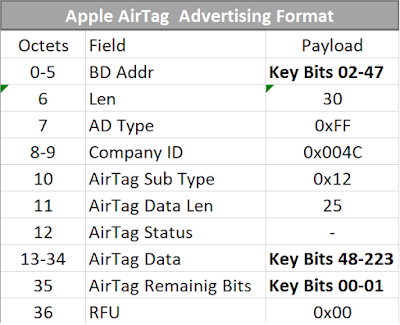
Secondly, AirTags internally do not implement a secure environment and thus do not use any form of authentication of their broadcasts. All they broadcast over Bluetooth is a time-changing P-224 (28 bytes) public key.
The key is not authenticated.
In practice this means this is a random-looking sequence of 28 bytes, which Apple takes at a face value, transports, stores, and offers to anyone producing the matching private key.
The lack of authentication of the originator makes it extremely easy to build any device for any purpose, leveraging the Apple FindMy system. For example, as Fabian Bräunlein has demonstrated recently, you can build an ESP32-based "tag" and use it to leak data, taking advantage of the Apple's FindMy crowdsourced global network. The lack of authentication also allows people to modify the tags e.g., to disable their built-in buzzers, so they stay silent and stealthy forever.
To me the real value of the AirTags would be the trust, underwritten by the Apple brand. But for that to happen there would need to be a complete chain of trust implemented, with the broadcast key signed by Apple and the tag being physically tamper-proof.
People may argue Apple's design decisions were limited by the size of the Bluetooth primary advertising PDU. This was true for so called legacy advertising (Bluetooth 4.x), but since Bluetooth 5 (December 2016) we have had the Extended Advertisements, offering up to 255 bytes (up from 37) in a single advertisement and up to 1650 bytes when chained. There clearly would be enough room to add an authenticating signature to the broadcast public key. Why Apple opted for the short legacy format is a mystery to me, as it means my iPhone, alongside all iPhones on Earth, are now willing to transport any properly formatted Bluetooth advertisements, regardless if originated by a genuine AirTag or something entirely different.
Comments
Post a Comment